Access sorted. Security strengthened. IDAM without the rework
Consultancy
From confusing licensing and feature gaps to failed logins and security risks, we help you design and implement the right IDAM solution for your needs. Faster, safer and without the guesswork.
Book your IDAM ConsultationTRUSTED BY GLOBAL ORGANISATIONS
Results we’ve delivered from our assessments
70% Reduction
Time to restore service cut by 70%
67% Cost Optimisation
Licence costs optimised by removing over-spec’d features
100% Login Success
For users requiring bespoke scripts
100% Seamless User Migration
With existing credentials intact
Struggling to make sense of it all?
Fragmented identity systems don’t just frustrate users, they create security holes and compliance headaches.
Does this sound familiar?
- Unsure what features you actually need or how to implement them
- Multiple identity services with fragmented user experiences
- Poor visibility, inconsistent access control and reporting headaches
- Escalating license costs with no clear insight or path to control spending
- Internal teams who can’t handle complex code scripts or custom integrations
- Risks from poor policy enforcement or inconsistent identity standards
We help you
- A tailored, secure and scalable IDAM setup that matches your business
- Faster implementation with fewer mistakes and better security
- An IDAM service designed to meet your business needs
- A fully configured and secured IDAM tenant
- Custom workflows and action scripts built for complex use cases
- Social sign-on integration across leading identity platforms
- Deep integration expertise with EntraID, AWS Cognito, Okta, Auth0 and more
- Clear licensing plans. No overpaying for what you don’t need
- Real SSO and consistent access for workforce and external
Secure, scalable access, without the complexity
A streamlined identity solution that reduces admin, increases visibility and locks down risk.
- Single sign-on across services and platforms
- Real-time threat detection and prevention (~100%)
- 96% reduction in admin load through self-service
- Standardised login flows for workforce and customers
- One access log, one source of truth for audit and reporting
- Clear policies for internal, external, and third-party users
- Full traceability and enforcement of security standards

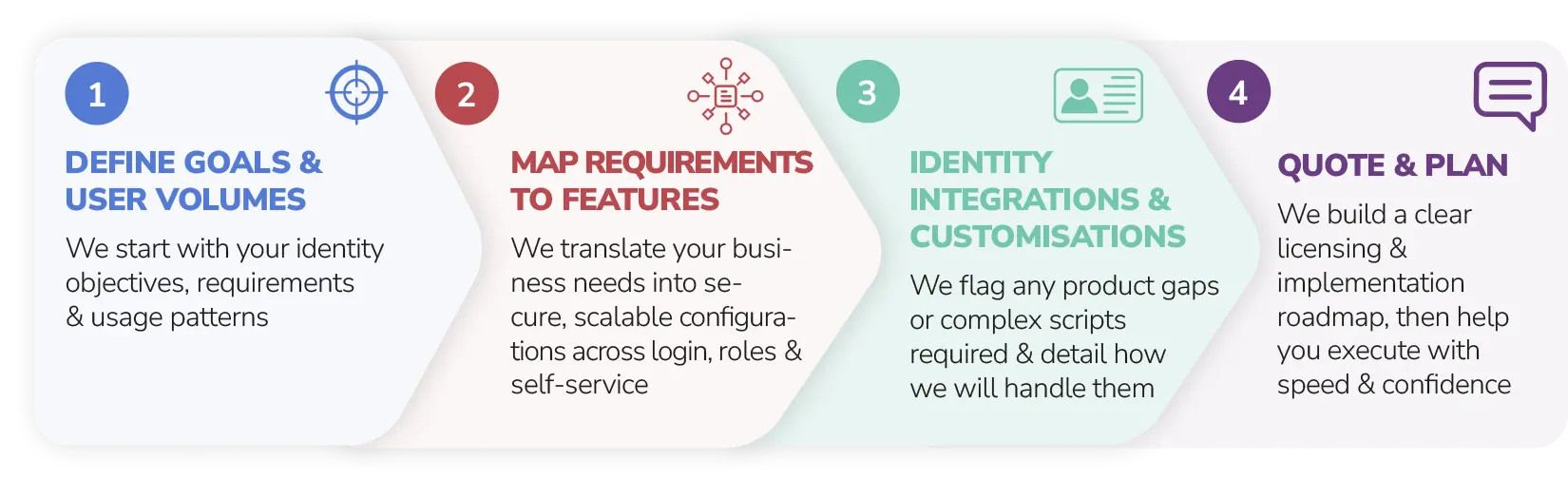
How it works. Our process
We simplify complex identity challenges so you get a secure, scalable setup designed around your users, not just your tools.
They knew what features we actually needed, what we didn’t and how to get it live without disrupting our users
Tech Lead. Regulated Enterprise